Noscript is an awesome advanced Firefox and Chrome extension for privacy and avoiding malicious activity in your browser and we highly recommend it.
However, when script blocking is turned on, by default it will break many sites you visit until you change some settings and start allowing some of the functional content to come through. If you need a very high level of privacy via script blocking, you can just leave full script blocking at the default settings. If you’re just using it day to day and want sites to be pretty functional, keep reading.
The main key to using noscript is being able to identify or at least guess what scripts are worth allowing and which ones aren’t.
Tip 1 – Turning on script blocking
First things first. Sometimes people don’t realize this, but simply installing noscript doesn’t actually do much. To start blocking scripts, you have to click on it and select the option to “Forbid Scripts Globally”.
Tip 2 – Getting core functionality working on most sites.
Once “Forbid Scripts Globally” is switched on, the first thing you can do to make using noscript easier is to open the options and check this setting:
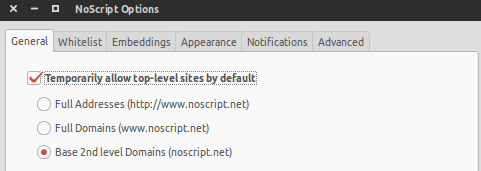
Allowing the base 2nd level domain like that will at least allow the main scripts from the domain you’re on to come through.
Tip 3 – Common scripts to allow (trust)
When you first start surfing with noscript, it’s pretty eye opening just how many scripts some sites use.
The problem is some of the sites you probably visit every day have so many damn scripts it’s hard to tell what exactly to allow to make things work.
A typical scenario is you land on an article on a ridiculously script heavy site like HuffingtonPost or PCWorld and want to watch a video, but the video is blocked by noscript so it won’t play. Now you click on the noscript icon, but sites like that with sometimes upwards of 70+ scripts, how do you know which one controls the damn video???
If you’ve followed Tip 1, The next thing to do is look in the list of blocked scripts for domains with ‘cdn’ in them and allow those. A CDN is just something many sites use to offload certain static content such as images and distribute to various servers around the world for faster loading times. This has become increasingly common over the past few years.
Also look for shortened versions of the primary domain. Those are usually safe to allow as well if you trust the site. Using the HuffingtonPost example, key examples of this to allow are huffpost.com and huffpo.net. Also aolcdn, which serves a lot of their functional content since AOL owns the site.
Other stuff that can be useful to allow is:-
- akamai
- cloudfront.net (usually preceded by a long string of letters and numbers)
- jqeurytools.org
- code.jquery.com
- disqus (a common commenting platform…enable this to see user comments on some sites)
- intensedebate (same as disqus)
For getting a video to work, try looking for the usual suspects to allow:
- youtube
- youtubeeducation
- vimeo
- livelink
Also look for domains that might be related to a news site…abc, nbc, bbc, cbc, aljazeera, rt, and domains that look like local news station call letters (kxci, wnyc, etc.)
googleusercontent is another one that’s sometimes necessary to allow for functionality as it’s usually related to Google’s Pagespeed Service, which is a CDN/optimization service Google offers that sites can use to speed up their site.
Tip 4 – Common scripts to leave blocked since they won’t affect functionality.
For the most part, none of the following scripts will help in viewing/using a site, so not much point in even bothering to allow them. They’re all just tracking, advertising, or analytics scripts. You’ll see them over and over again almost everywhere.
- google-analytics
- googletagservices
- doubleclick
- scorecardresearch
- quantserve
- newrelic
- adsonar
- gravity
- chartbeat
- facebook and twitter (usually just allows for sharing functionality and ‘like’ counters, although sometimes controls facebook comment integration and twitter feeds)
- demandbase
- gigya
- brightcove
- viglink
Those things alone should at least get you to a more functional state on a site without compromising much privacy. Beyond that it’s typically a matter of trial and error and experience at guessing what certain scripts do. Over time as you permanently allow certain scripts, your stored noscript settings will build up to the point where most things are functional right away.
Sometimes if you really need to see the content and can’t figure it out, the easy (but less safe) thing to do is just temporarily “allow all” for a page. Sometimes you’ll need to hit that two or three times due to scripts blocking other scripts. After you’re done, it’s advisable to revoke those permissions and close and reopen your browser after clearing your history, cookies, cache, and LSO (long term flash) cookies via an extension like Better Privacy.
We highly recommend using noscript alongside PrivacyBadger or Ghostery, because even when you “temporarily allow all” something in noscript, those other extensions will still block all or most of the advertising, tracking, and analytics stuff.
It’s a complex script, but worth using if you’re ok with getting past the initial headache of picking through scripts. And of course if you’re not sure, you can go ahead and install it and toggle script blocking on and off whenever you feel like it.
Final Tip #5 – Even if you don’t like NoScript’s script blocking, leave it installed.
If you decide script blocking is too much of a hassle, rather than uninstall it, you should consider just switching to “Allow Scripts Globally”. Even when allowing all scripts, NoScript still provides a few other protections such as protection against cross-scripting and click-jacking.


1 Comment
Thx for this. I tried noscript last week but got very frustrated with the number of sites that were broken so turned it off. im going to give it another go and persist a little more.