What is Tor?
 Tor stands for the name of the original project, The Onion Router and is a non-profit organisation that conducts research and development into online privacy and anonymity.
Tor stands for the name of the original project, The Onion Router and is a non-profit organisation that conducts research and development into online privacy and anonymity.
Tor bounces internet users and websites traffic through “relays” run by thousands of volunteers across the globe making it almost impossible to trace the location of the user or source of any data.
The original technology was developed by the US Navy and subsequent backers have included the US State Department and diverse lobby groups like the Electronic Frontier Foundation. At first the emphasis was on protecting users privacy from corporations rather than Governments but all that has changed in recent years and even more dramatically after the NSA surveillance revelations in 2013.
How Does Tor Work?
Firstly, download the software and install it . Then on opening, Tor runs a customized version of Firefox portable and you can surf the net anonymously.
Data packets on the Tor network take a random pathway through several relays, encrypting it each time. Each relay along the way knows only which relay gave it data and which relay it is giving data to. No individual relay ever knows the complete path that a data packet has taken.
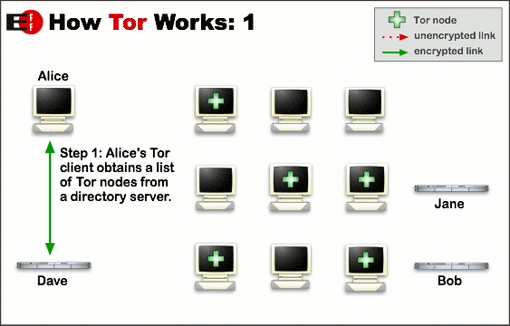
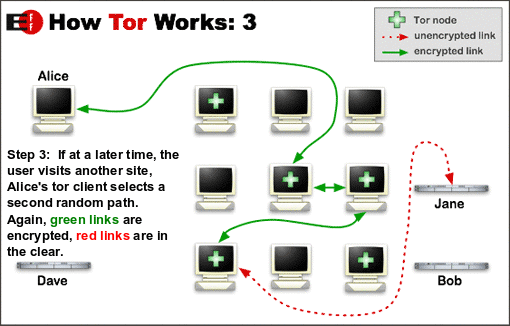
Tor uses the same circuit for connections that happen within the same ten minutes or so. Later requests are given a new circuit, to keep people from linking your earlier actions to the new ones.
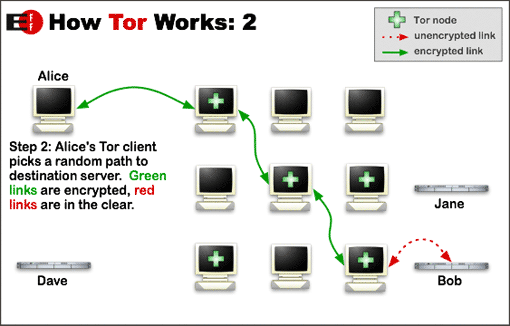
Because each relay sees no more than one hop in the circuit, neither an eavesdropper nor a compromised relay can use traffic analysis to link the connection’s source and destination.
Who Uses Tor?
The Tor project team identify five main groups of people who use Tor when accessing the internet.
- Ordinary users or people like you and me who who use Tor to protect their privacy and dignity online.
- Businesses who use it for confidentiality and research.
- Activists and whistleblowers to reports on abuse and corruption from ‘danger zones’
- Journalists for protection of research and sources.
- Military or Law enforcement personnel to protect their communications, investigations, and intelligence gathering online.
Tor and the Dark Web
The promise of privacy and anonymity inevitably attracted a whole darker set of users. Not only can Tor hide users identities but also host websites which can only be accessed by people on the Tor network and has led to the so called “dark web” of anarchy and criminality.
You may have heard of the the Silk Road, an underground illegal-drugs marketplace which was a hidden site only accessible through Tor and has since been shutdown. Black Market Reloaded which has been accused of facilitating illegal arms dealing as well as drug purchases is another Tor hosted website.
Pros and Cons
Since the revelations of NSA spying in 2013 the number of users of Tor has increased from around 500,00 to over 4 million and it’s use will likely continue to grow.
On the plus side Tor is free and because it’s a distributed network is almost impossible to shut down or attack. It’s also very secure and private.
However many will find it slow and restrictive, compared to a VPN as it can be very, very slow indeed. It’s unsuitable for P2P downloading or streaming geo-restricted media content not only because it is too slow but volunteers running the exit relays may be held accountable for any copyright violations so using Tor for those purposes is heavily frowned upon.
Perhaps more importantly, attacks on the Tor network are becoming increasing common place and law enforcement agencies are rapidly catching up with the technologies used and are actively seeking ways to compromise the project’s anonymising capabilities.
Use the Latest Version
Beware! Attacks on the Tor network are becoming more and more frequent so you should always make sure you are at least running with the latest version of the software.
Please add your comments below or in the related discussion topic of our forum.
